In the digital age, data is one of the most valuable assets a business can have. Whether it’s customer records, employee files, financial data, or proprietary information, all data carries a level of sensitivity and risk. When that data is no longer needed, it must be disposed of properly. This is where certified data destruction comes into play.
Certified data destruction is the secure, verified process of permanently eliminating data from storage devices. It ensures that no one can recover or misuse the data after it has served its purpose. This guide explores what certified data destruction is, why it matters, the methods used, compliance standards, and how to choose a reliable provider. We’ll use LSI keywords such as “secure data disposal,” “data erasure methods,” “hard drive shredding,” “HIPAA compliance,” and more to ensure a comprehensive, SEO-optimized resource.

What Is Certified Data Destruction?
Certified data destruction is the secure, verifiable process of permanently eliminating data from storage devices in accordance with industry-recognized standards and legal regulations. Unlike simple file deletion or formatting—which often leaves data recoverable—certified data destruction uses approved methods such as software-based overwriting, degaussing, physical shredding, or cryptographic erasure to ensure that sensitive information is completely irretrievable.
This process is essential for protecting personal, financial, medical, and confidential business data from unauthorized access, data breaches, or misuse. Organizations receive a Certificate of Data Destruction (CoD) as official proof that data was destroyed properly, helping them stay compliant with regulations like HIPAA, GDPR, and FACTA, and reducing the risk of legal penalties and reputational damage.
Recent Post: How UK Businesses Can Securely Dispose of Old IT Equipment and Recycle Responsibly
Why Certified Data Destruction Matters?

- Ensures Complete Data Elimination
Data is permanently destroyed and cannot be recovered by any method. - Prevents Data Breaches
Eliminates the risk of unauthorized access to sensitive information. - Meets Legal & Regulatory Requirements
Complies with strict laws like HIPAA, GDPR, FACTA, GLBA, and more. - Protects Brand Reputation
Avoids negative press, loss of trust, and customer churn caused by data leaks. - Provides Verifiable Proof
A Certificate of Data Destruction (CoD) confirms the process was performed correctly. - Supports Audit & Due Diligence
Demonstrates responsible data management during internal and third-party reviews. - Safeguards Confidential Business Data
Protects intellectual property, trade secrets, and operational information. - Reduces Legal Liability
Helps avoid lawsuits, fines, and penalties related to improper data disposal. - Boosts Customer Trust
Shows clients and stakeholders that their information is handled responsibly.
Regulatory Frameworks and Industry Standards!
| Regulation/Standard | Industry | Requirement |
| HIPAA | Healthcare | Secure destruction of patient records |
| GDPR | General (EU) | Right to erasure; proper data disposal |
| FACTA | Financial | Disposal Rule enforcement |
| NIST 800-88 | All | Guidelines for media sanitization |
| DoD 5220.22-M | Government | Multiple overwriting passes for deletion |
What Are the Methods of Certified Data Destruction?
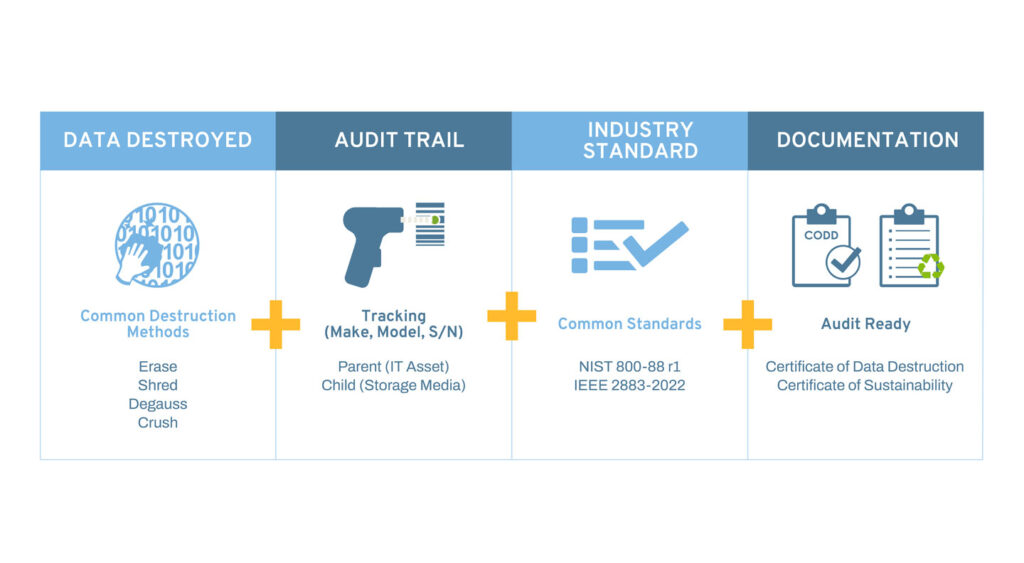
Physical Destruction:
Physical destruction is one of the most definitive methods of certified data destruction. It involves damaging the storage device beyond repair, making data recovery physically impossible. This method is often used for devices that are obsolete, damaged, or not intended for reuse. Techniques include shredding, where the device is ground into tiny pieces; degaussing, which demagnetizes the drive and disrupts the stored data; and incineration, where the entire device is burned at high temperatures.
Software-Based Data Erasure:
Software-based data erasure uses certified tools to overwrite the entire storage medium with random data multiple times. Unlike simple deletion or formatting, which can leave traces behind, this process meets stringent standards such as NIST 800-88 Rev. 1 and DoD 5220.22-M. Leading tools like Blancco, BitRaser, and KillDisk verify and document the success of each erasure.
Cryptographic Erasure:
Cryptographic erasure is used when data is encrypted at rest. It involves deleting or destroying the encryption keys that protect the data, making it unreadable and inaccessible. Once the keys are removed, the encrypted data cannot be decrypted, even if the storage device remains intact. This method is fast and efficient, especially in large-scale enterprise environments or cloud-based systems.
Data Masking and Obfuscation:
While not a standalone certified destruction method, data masking or obfuscation can be part of the early stages of data sanitization. These techniques involve replacing sensitive information with fake or scrambled data to prevent unauthorized access. They are commonly used in testing, development, or training environments where the original data is not required.
Hybrid Approaches:
In some cases, certified data destruction providers may use a combination of methods depending on the device type, data classification, and compliance obligations. For example, a high-risk enterprise may choose software erasure followed by physical shredding to ensure multi-layered protection.
What Is the Certificate of Destruction for GDPR?
A Certificate of Destruction (CoD) is a formal document issued by a certified data destruction provider confirming that personal data has been securely and permanently destroyed in full compliance with the General Data Protection Regulation (GDPR) requirements. Under GDPR, organizations are obligated to protect the privacy and rights of individuals by ensuring that personal data is not only securely stored but also properly disposed of when no longer needed.
The CoD serves as legal proof that the data destruction process followed approved methods—such as those outlined in NIST 800-88 or other industry standards—and that the data can no longer be accessed, recovered, or misused. This certificate typically includes details such as the date of destruction, method used, device information, and signatures from authorized personnel. Maintaining a CoD is critical for GDPR compliance, as it demonstrates accountability and transparency during audits or regulatory investigations.
Related Post: The Ultimate Guide to Certified Data Destruction and IT Recycling in the UK
How can I verify a vendor’s destruction methods are certified?
- Check Industry Certifications: Look for recognized certifications such as NAID AAA, ADISA, ISO 14001, or R2. These certifications indicate the vendor meets strict requirements for secure data destruction.
- Request Documentation: Ask the vendor to provide their certification documents and proof of compliance with standards like NIST 800-88 or DoD 5220.22-M.
- Review the Certificate of Data Destruction (CoD): After destruction, a reputable vendor will provide a detailed CoD that includes the destruction method, device details, timestamps, and signatures.
- Evaluate Security Processes: Confirm the vendor has secure chain-of-custody procedures, such as locked bins, GPS-tracked transport, and secure facilities monitored 24/7.
- Look for Independent Audits: Trusted vendors undergo regular third-party audits and assessments. Request audit reports or evidence of ongoing compliance checks.
- Check Customer References and Reviews: Feedback from other clients can provide insight into the vendor’s reliability and adherence to certified methods.
What are the most trusted data destruction software tools?

- Blancco: A market leader in data erasure, Blancco provides certified software that meets global standards like NIST 800-88, DoD 5220.22-M, and GDPR requirements. It offers detailed reporting and verification, making it popular with enterprises and governments.
- BitRaser: Known for its user-friendly interface, BitRaser offers certified data erasure with compliance for over 20 global standards. It supports multiple device types and generates tamper-proof certificates of destruction.
- KillDisk: A robust software tool that supports multiple overwrite standards and produces audit-ready reports. It’s widely used for desktops, servers, and external drives.
- WhiteCanyon WipeDrive: This tool is trusted for its secure erase algorithms and extensive reporting capabilities. It supports certifications for HIPAA, GDPR, and other regulatory frameworks.
- Active@ KillDisk: Another reliable tool that offers certified erasure and works on various platforms, including Windows and Linux.
Interesting Fact: Why Secure Data Destruction Is Non-Negotiable in 2025
FAQs
What Does Certified Data Destruction Mean?
Certified data destruction refers to the process of permanently and securely erasing or physically destroying data on storage devices in accordance with recognized industry standards and legal regulations.
Is Certified Data Destruction Legally Required?
In many industries, certified data destruction is legally required to comply with regulations such as HIPAA, GDPR, GLBA, and others that mandate secure disposal of sensitive personal or financial data.
What’s the Difference Between Deletion and Certified Destruction?
Deletion or formatting typically removes references to data but does not erase the actual data, making it potentially recoverable with the right tools. Certified destruction involves methods like software overwriting or physical destruction that permanently erase data beyond recovery, with documented proof to verify compliance.
What Should a Certificate of Data Destruction Include?
A Certificate of Data Destruction (CoD) is an official document that proves data was securely and permanently destroyed in compliance with recognized standards. It typically includes details such as the device type, serial number, destruction method used, date and time of destruction,and the names of the responsible technicians.
How Long Does Certified Data Destruction Take?
The time for certified data destruction varies depending on the method and volume of devices. Software-based erasure can take from minutes to several hours per device, depending on size and complexity, while physical destruction is usually completed much faster.
Conclusion:
Certified data destruction is not just a security measure, it’s a business necessity. With rising threats, tighter regulations, and growing public awareness, companies must take a proactive approach. Whether you’re handling medical records, customer emails, or internal reports, secure data disposal helps you stay safe, compliant, and reputable.


